Prerequisites for Installation
- Kubernetes Cluster: K8s cluster 1.27+.
-
Domain to map the ingress of the AI Gateway along with certificate for the domain. (also any ingress controller or istio gateway you are using)
This Domain will be referred as Gateway Endpoint Host in our documentation.
-
TrueFoundry SaaS Account: Sign up and create a new tenant on TrueFoundry SaaS by logging in to TrueFoundry. You will receive an invitation on your email to verify your email and login.
While signing up, you will sign up by entering your company name. This company name will be used as the tenant name. Your control plane URL will be
https://<YOUR_COMPANY_NAME>.truefoundry.cloud. If your company name isexample-company, then your control plane URL will behttps://example-company.truefoundry.cloud. -
Egress access to TrueFoundry SaaS (Control Plane URL is from Step 3):
- Control Plane:
https://<CONTROL_PLANE_URL>(e.g.,https://example-company.truefoundry.cloud) - NATS:
wss://<CONTROL_PLANE_URL>:443(e.g.,wss://example-company.truefoundry.cloud:443) - OpenTelemetry:
https://<CONTROL_PLANE_URL>/api/otel/v1/traces(e.g.,https://example-company.truefoundry.cloud/api/otel/v1/traces)
CONTROL_PLANE_URL: Your control plane URL in the formatcompany-name.truefoundry.cloud(without thehttps://prefix). This is the same as your tenant name from Step 3. For example, if your company name isexample-company, then your CONTROL_PLANE_URL isexample-company.truefoundry.cloud. - Control Plane:
- Image Pull Secret: Image pull secret from TrueFoundry team to enable pulling the truefoundry images from the private registry.
Installation Instructions
1
Create Gateway Endpoint in TrueFoundry SaaS
Create an entry for Gateway Endpoints by logging into the TrueFoundry SaaS platform.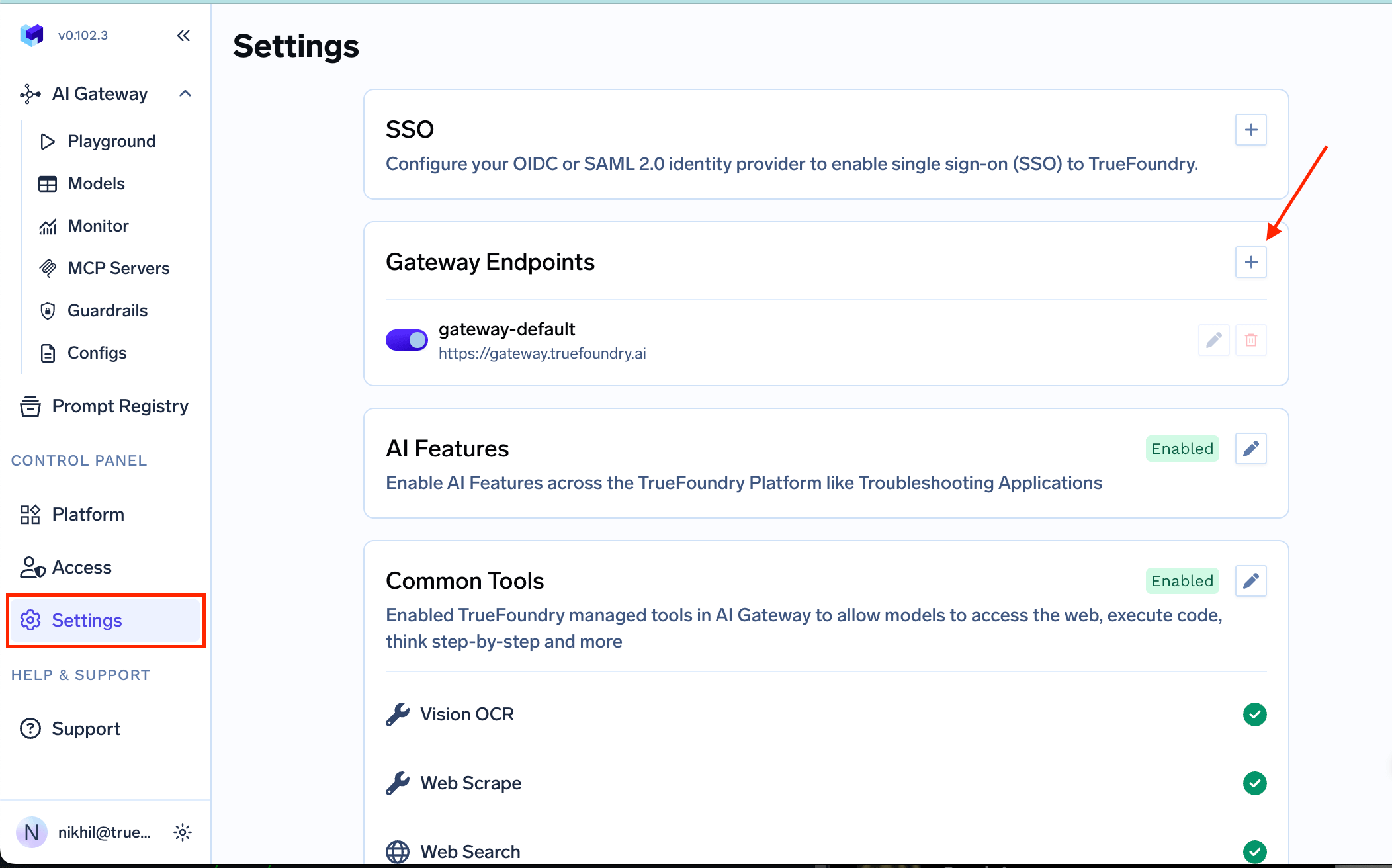
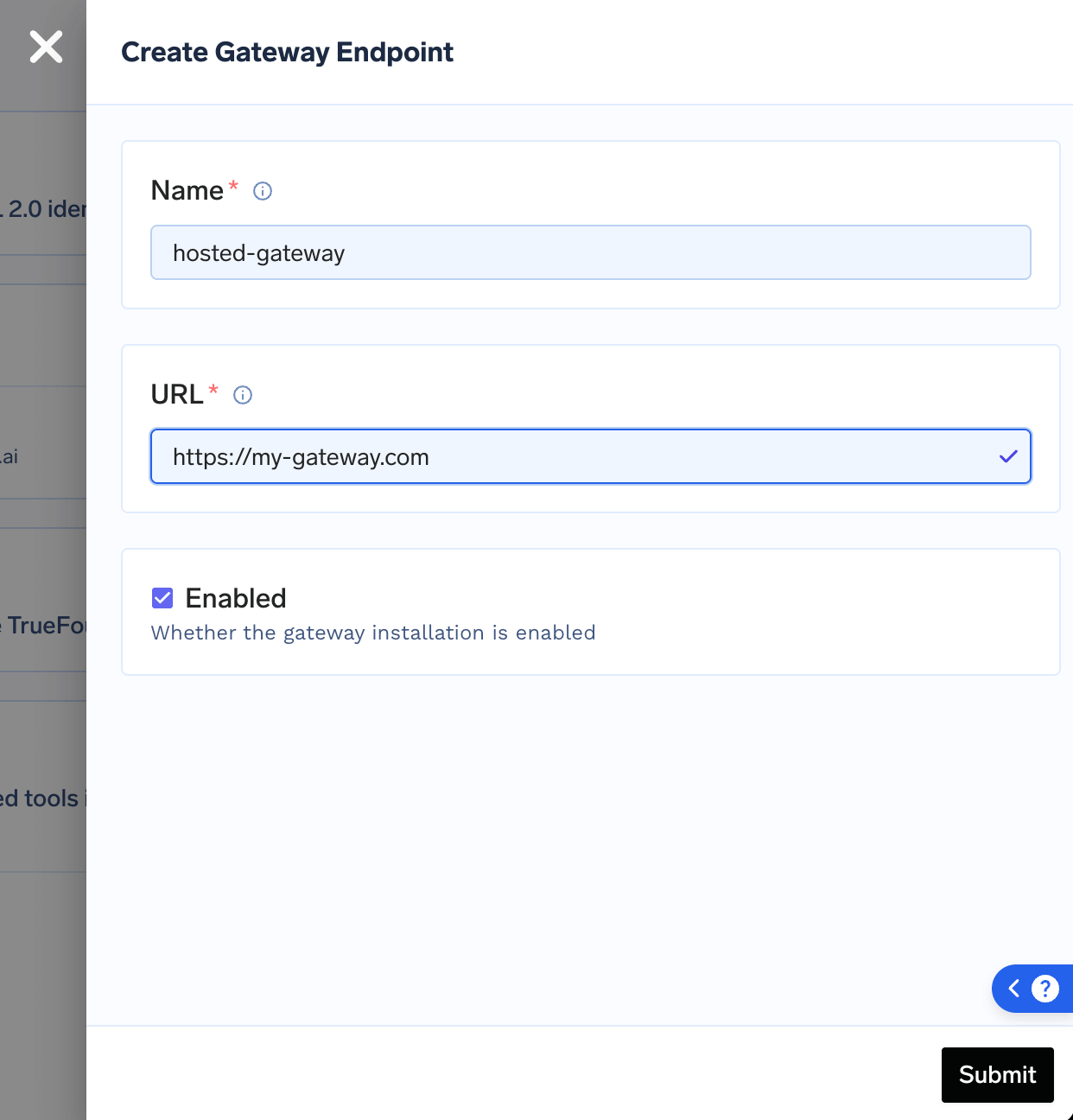
- Navigate to Settings -> Gateway Endpoints

- Create a new gateway endpoint with a unique name
- Enter the URL where you will be deploying your gateway

The gateway installation name you provide here will be used in step 3 to obtain the TFY_API_KEY.
2
Obtain the TFY_API_KEY
To obtain the TFY_API_KEY, you need to run the following curl command:In this command: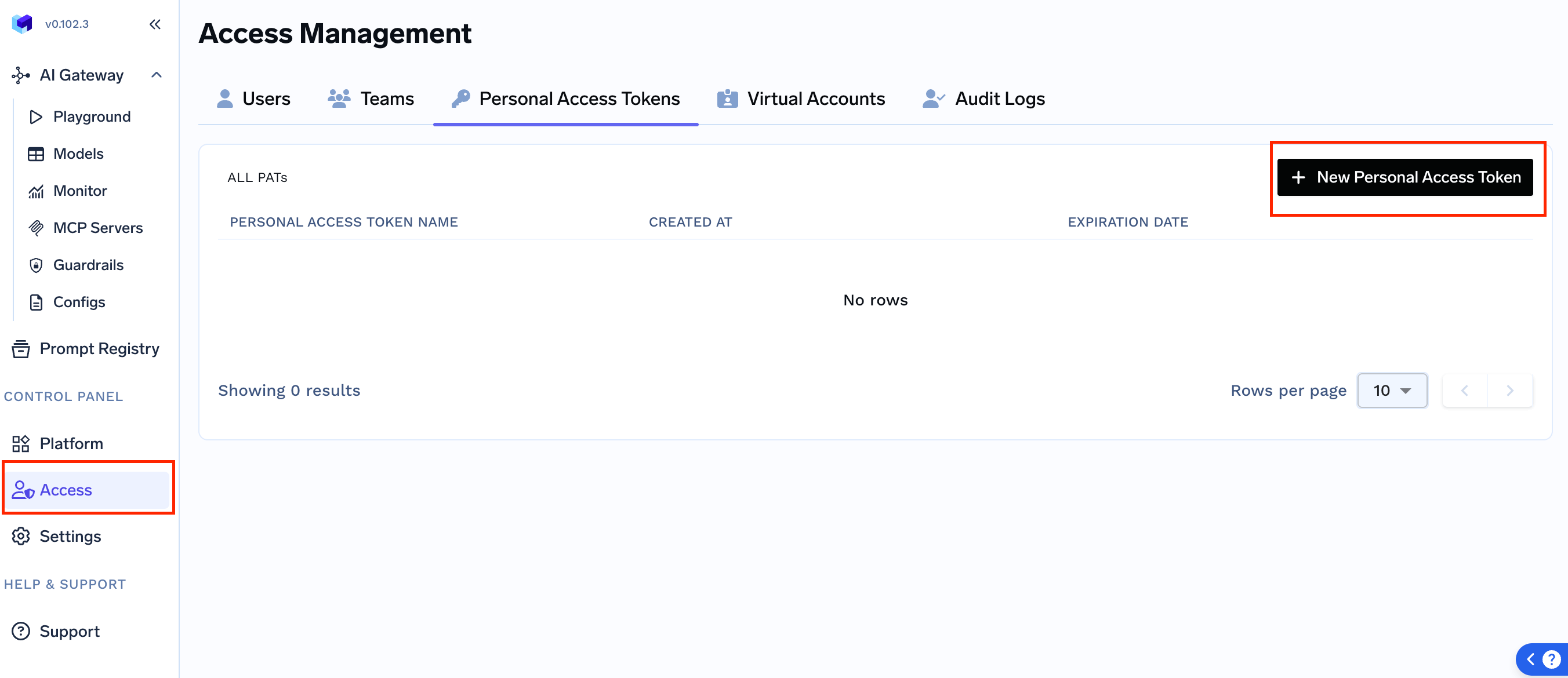
- CONTROL_PLANE_URL: Your control plane URL in the format
company-name.truefoundry.cloud(without thehttps://prefix). For example, if your company name isexample-company, then useexample-company.truefoundry.cloud. This is the same as your tenant name from Step 3. - PERSONAL_ACCESS_TOKEN: Your personal access token. Create a token by going to Access -> Personal Access Tokens

- GATEWAY_INSTALLATION_NAME: The gateway installation name that was given in step 1.
TFY_API_KEY which you will use in the next step.3
Create Kubernetes Secrets
We will create two secrets in this step:
- Store the TFY_API_KEY
- Store the Image Pull Secret
Create Kubernetes Secret for TFY_API_KEY
Create Kubernetes Secret for TFY_API_KEY
We need to create a Kubernetes secret containing the TFY_API_KEY obtained in the previous step.Apply the secret to the Kubernetes cluster (Assuming you are installing the gateway plane in the
truefoundry-creds.yaml
truefoundry namespace)Create Kubernetes Secret for Image Pull Secret
Create Kubernetes Secret for Image Pull Secret
We need to create a Image Pull Secret to enable pulling the truefoundry images from the private registry.Apply the secret to the Kubernetes cluster (Assuming you are installing the gateway plane in the
truefoundry-image-pull-secret.yaml
truefoundry namespace)4
Create Helm Chart Values file
Create a values file as given below and replace the following values:You can find full list of supported values here.
- CONTROL_PLANE_URL: Your control plane URL in the format
company-name.truefoundry.cloud(without thehttps://prefix). This is the same as your tenant name. For example, if your company name isexample-company, then useexample-company.truefoundry.cloud. - TENANT_NAME: The tenant name (same as the company name you used to create your account on TrueFoundry SaaS)
- GATEWAY_ENDPOINT_HOST: The domain where you will expose the gateway endpoint (e.g.,
gateway.example.com)
truefoundry-values.yaml
5
Install the Helm Chart
Install the TrueFoundry Helm chart using the values file created in the previous step:
6
Verify the Deployment
Verify that all pods are running:You can verify the deployment by checking the health of the gateway endpoint by running the following command:A successful response indicates that the gateway plane is deployed and running correctly.
Accessing the Gateway
You can now access the gateway endpoint from the TrueFoundry SaaS UI by selecting the gateway endpoint from the dropdown in Playground as shown below: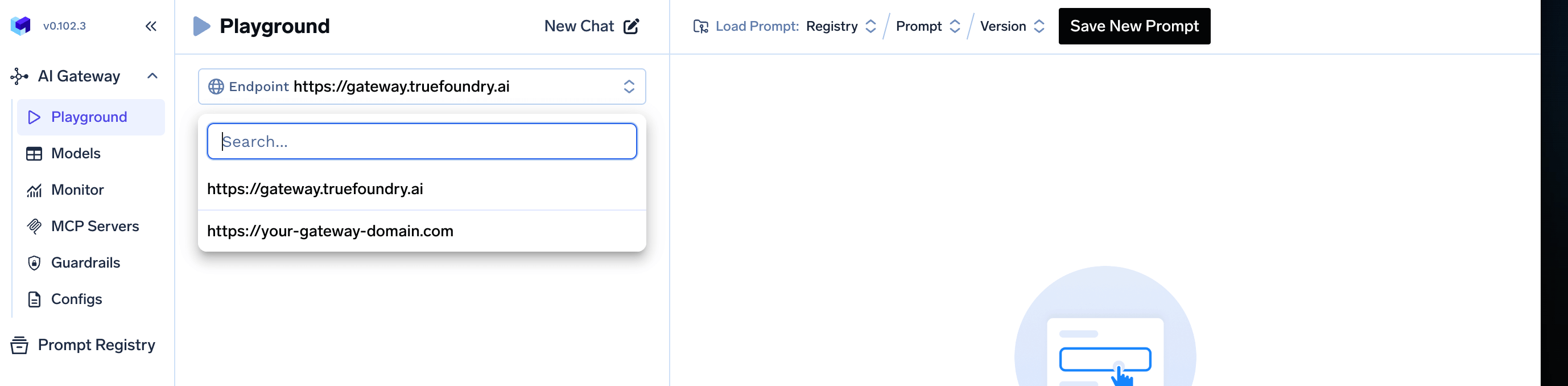
https://<GATEWAY_ENDPOINT_HOST> and can be used to make LLM inference requests through the TrueFoundry AI Gateway.